Why CFW?
Features
Fine-Grained Access Control
You can control access traffic in all directions and block intrusions in real time. Access from the Internet, between VPCs, or at a specific granularity can be controlled.

Control Server Originated Traffic
You can check external connections, identifying and blocking malicious access.
Statistics about servers requesting external connections are displayed on the CFW console, helping you identify malicious or intruded servers.
Intrusion Detection and Prevention
CFW's intrusion prevention engine detects and intercepts malicious traffic in real time to implement intelligent and accurate protection based on Huawei's network-wide threat intelligence.
For assets that can access the Internet, CFW can identify their attack surface and allow you to enable protection in a few clicks.
Log Audit and Traffic Visualization
All traffic is logged and can be presented in reports. You can audit events and trace threats back to their sources.
All of the traffic on your network is visualized.

Application Scenarios
Scenario
You can use CFW to perform security stocktaking on service assets accessible to the public network, and enable intrusion detection and prevention in one click.
Advantages
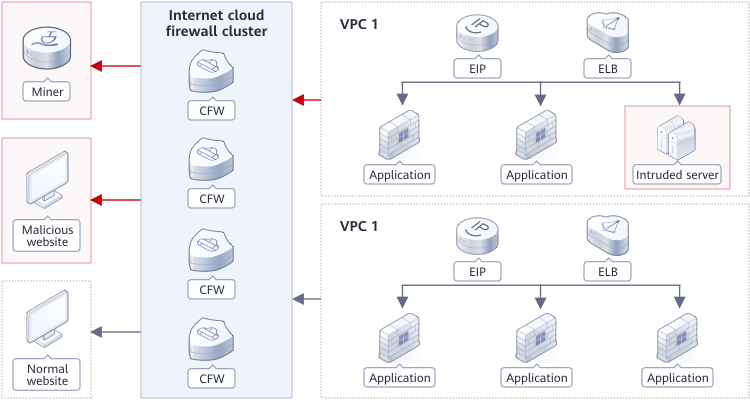
Scenario
You can implement domain-based precise control over server originated traffic.
Advantages
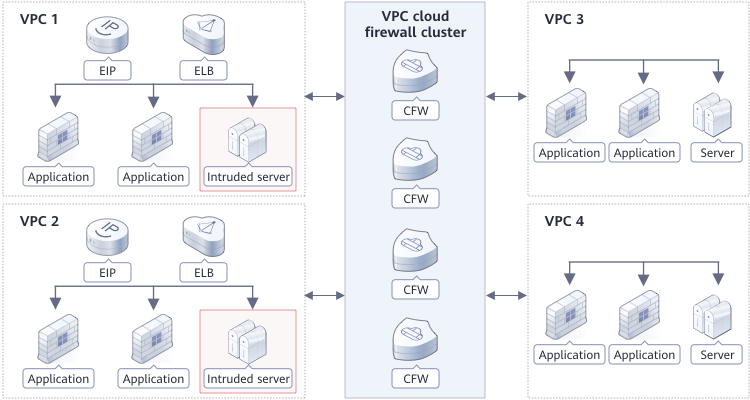
Scenario
Check inter-VPC traffic and control internal access.
Advantage

